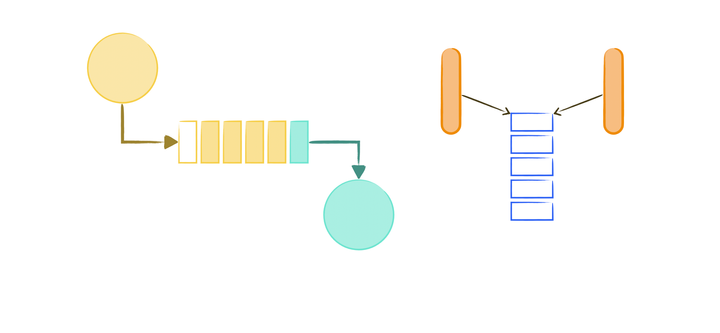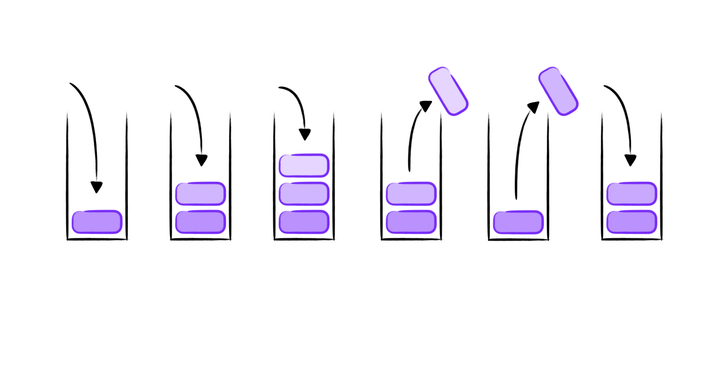

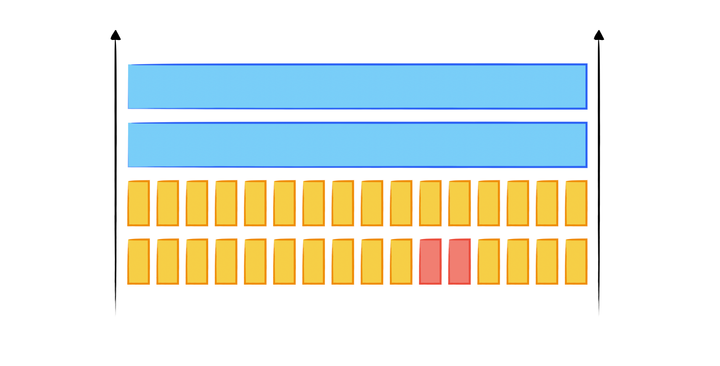
Buffer Overflow Attack from the Ground-up III: Canary
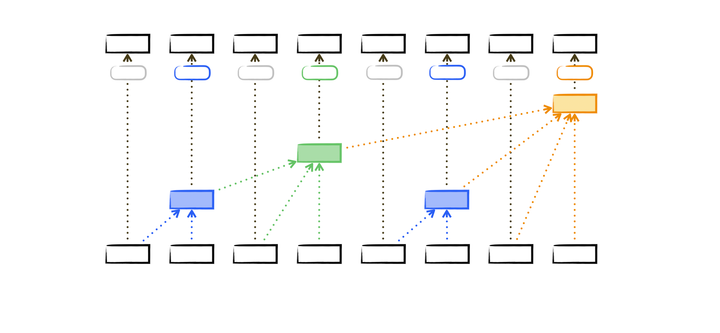
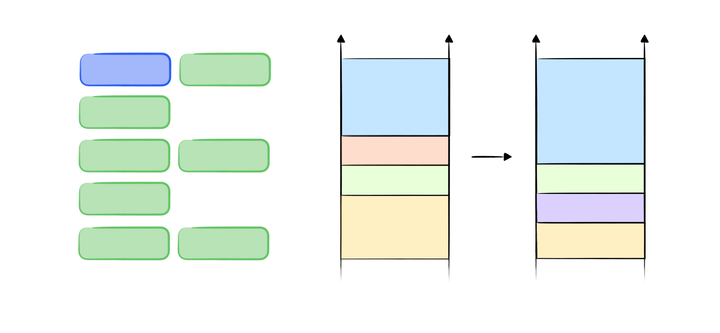
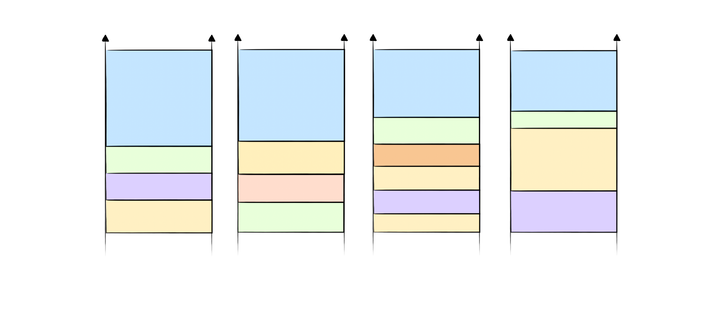
Binary Indexed Tree: A Data Structure that Can Enhance Query Performance in Arrays
Buffer Overflow Attack from the Ground-up II: Gadget and Shell Code Injection
Buffer Overflow Attack from the Ground-up I: Simple Overflow
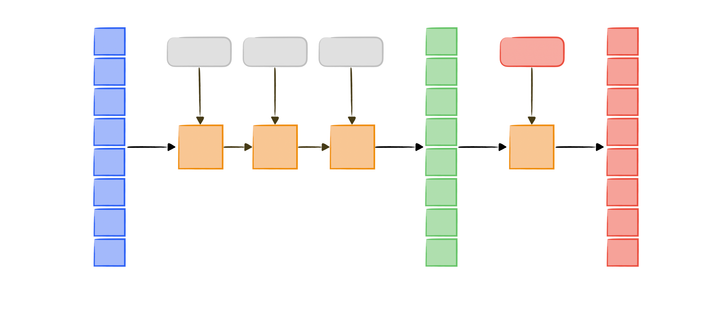
An Introduction to SHA256 Hash Extension Attack
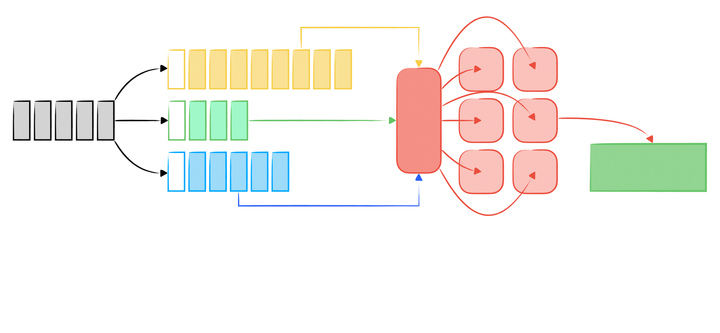
An Introduction to Kafka and Samza for Stream Data Processing
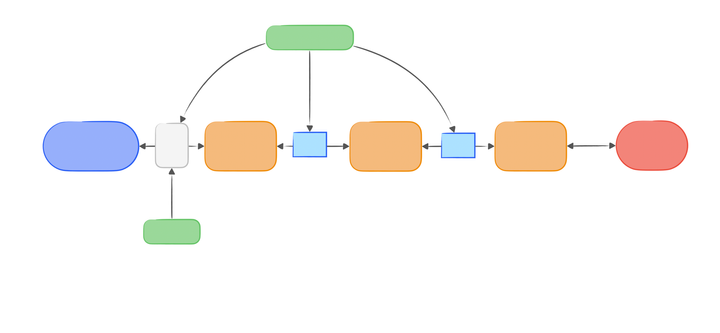
An Introduction of NestJS, a Node.js web/app server framework.
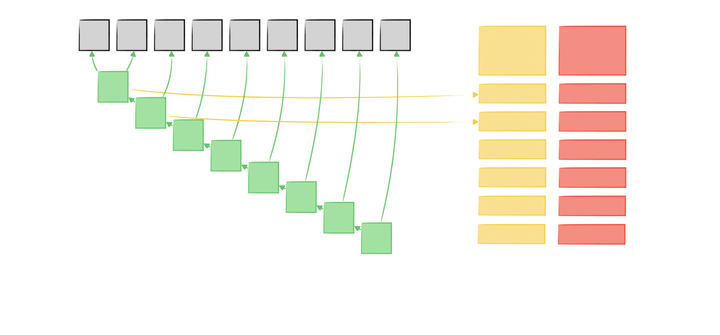
Prefix Sum with HashMap: Time Complexity Optimization
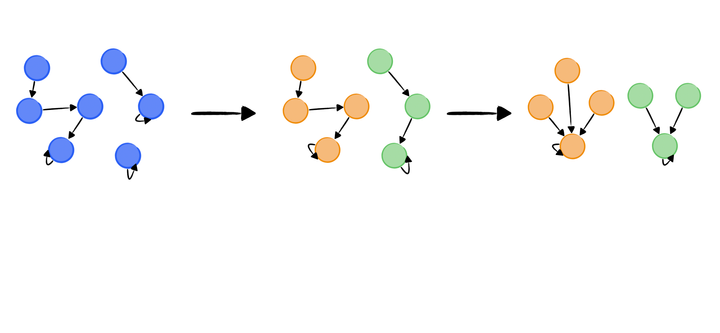
Disjoint Set: City Connection Problem
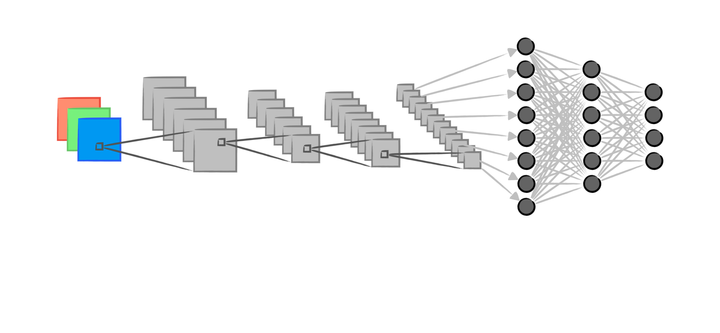
Neural Networks Series II: Forming Vision - How a Convolutional Neural Network Learns
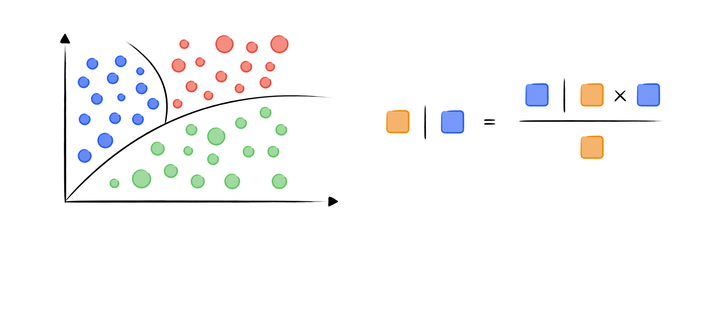
Understanding Naïve Bayes Algorithm: Play with Probabilities
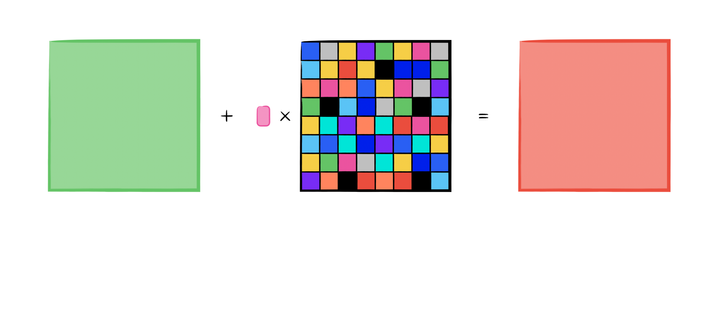
Gradient Attack: A Brief Explanation on Adversarial Attack
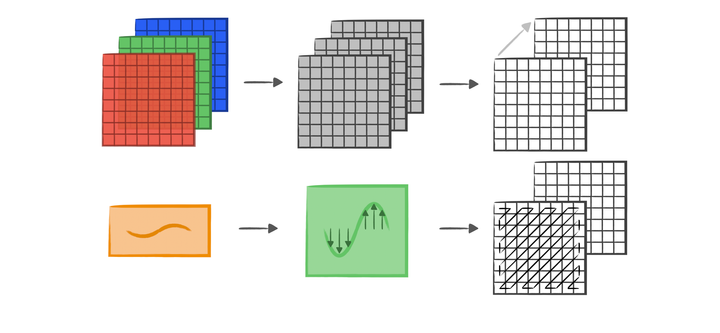
Implementing JPEG Image Compression Algorithm using MATLAB
RSA Digital Signatures and Public-Key Cryptosystems
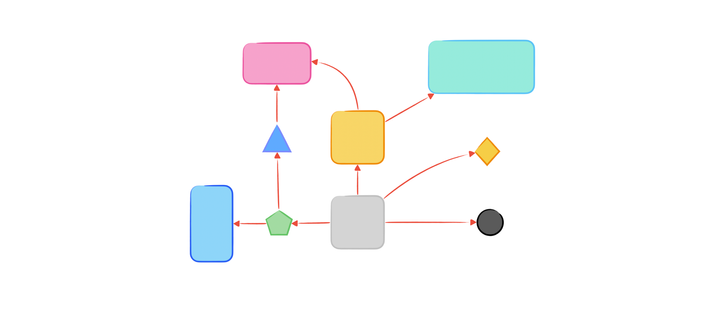
Front-end Walkthrough: Web Frameworks, JAMStacks and Native Apps
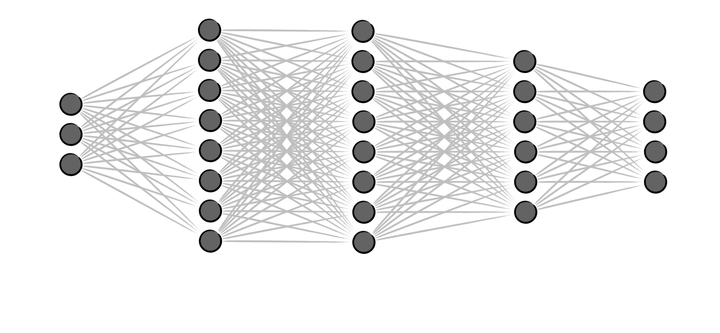
Neural Networks Series I: Loss Optimization - Implementing Neural Networks from Scratch
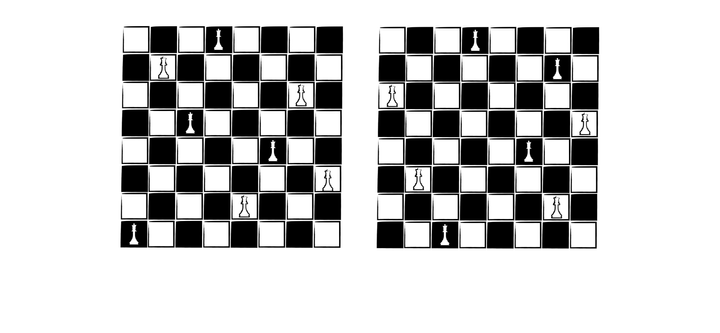
Eight Queens Problem: Classical Puzzles